Why is data center security important in the cloud?
- 2022-09-30
- 작성자 Haeyong Yang, Seyoung Kim



Data centers are secure facilities that offer services such as server computers and network lines. Tens of thousands of server computers operating in the data center store important customer information, and its stable operation is vital for the company's survival. With the recent increased amount of data generated by enterprises in line with the 4th Industrial Revolution, the amount of damage caused by cybercrime, such as hacking, has also been increasing exponentially. Today, data center security is no longer optional; it is an integral part of enterprises. In this report, we’ll look at three security areas of the data center: Security governance, infrastructure security, and application security.
Before explaining data center security
The concept and importance of the data center
Before talking about data center security, we must first understand the concept of data centers. A data center is a building or facility that offers server computers, network connections, and related services. Tens of thousands of server computers in data centers store vast amounts of information for browsing, shopping, and gaming. Its role is to gather and manage such information for stable operation.
[Wait!] Stable data center operation is vital for company survival
The stable operation of a data center, which stores important customer information, is directly tied to the survival of the company. The inclusion of factors like spare capacity, uninterrupted operations, and efficient air conditioning in data center tier classification (Data Center Tiers) underscores the central objective of data centers: to guarantee consistent and reliable service continuity. However, even with the guarantee of service availability, we face an entirely different level of risk when confronted with security issues such as hacking. And this is when the importance of data center security becomes increasingly vital.
Recently, in conjunction with the 4th Industrial Revolution, the amount of data generated by enterprises, including big data, AI, IoT, and autonomous driving, is further increasing, and the amount of damage caused by cybercrime is also growing exponentially. Today, data center security is no longer optional; it is an integral part of enterprises.
[Wait!] What are the components of data center security? Governance, infrastructure security, and application
There are mainly three components in data center security: Governance, infrastructure security, and application.
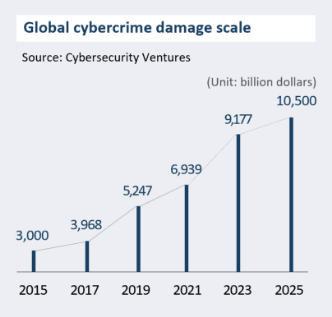
Source: Cybersecurity Ventures
(Unit: billion dollars)- 2015
- 3,000
- 2017
- 3,968
- 2019
- 5,247
- 2021
- 6,939
- 2023
- 9,177
- 2025
- 10,500
Security areas of data center
First, security governance
The term “governance” has a broad and vague definition of “a way to run the government that solves problems by building networks of common interests.” However, “governance” in data center security can be described in terms of policy aspects, such as physical security, regulations, standards, education, and approval processes. In other words, it is about creating policies, management systems, and processes for security regulation to establish a solid foundation for the data center
The security policy describes an organization's security objectives, the scope of the policy, asset classification, and management, but does not explain them in detail. For example, although the policy states that “transmissions of confidential documents or sensitive data must be encrypted,” it does not mention which encryption protocol should be used. The details are laid out in separate materials, such as guides, not in the policies. In addition, the data center is audited and certified by each certification body to meet its criteria, which includes security as an essential component. This is a testament to the fact that security is essential for the safe service and facility operation of data centers.
Types of domestic/international certification examination
| Type | Summary | Certification |
|---|---|---|
|
ISO27001 (Information Security Management System) |
|
BSI |
|
ISO27017 (Cloud Service Information Security Management System) |
|
BSI |
|
ISO27018 (Cloud Service Privacy International Standard) |
|
BSI |
|
ISO27799 (International Standard for Personal Health Information Protection) |
|
BSI |
|
CSA STAR (Cloud Security Alliance - Security, Trust, Assurance and Risk) |
|
BSI&CSA |
|
CSAP (Certified Secure Application Professional) |
|
KISA |
|
ISMS (Information Security Management System) |
|
KISA |
※ Samsung SDS data center has obtained the above seven certifications and is undergoing follow-up audits and renewals every year.
Second, infrastructure security
Data centers must ensure the safety of the server computers and networks that make up their architecture. In particular, security measures have become essential as the number of cloud environments that provide infrastructure resources, such as computers, storage, and networks, as services have increased.
Among them, let's look at “network separation,” which is the most powerful method of maintaining infrastructure safety recommended by experts. Network separation is a policy and infrastructure configuration technology separating networks into the Internet and business networks without the Internet. This is a method of physically or logically separating the network so that even if hackers break into a user's PC via the Internet, they cannot access important information in the system. Although it has a simple concept, the actual implementation is not as simple since it requires collaboration between security and related departments. Yet, once it works properly, the outcome is beyond the expectation.
[Wait!] Why network separation must be considered even in the complicated cloud environment
Even in terms of regulation, in accordance with the Personal Information Protection Act and the Information and Communications Network Act, network separation is mandatory for information and communication service providers with annual sales of KRW 10 billion or more. The recent cloud environment resources are interdependent. This tells us that traditional security measures of protecting network perimeters with firewalls alone are insufficient. Thus, shared resources need to be dynamically and automatically provisioned, and safety can be anticipated only when we take into account the logical stability of physically ambiguous security boundaries. This is why network separation technology must be considered even in complicated cloud environments.
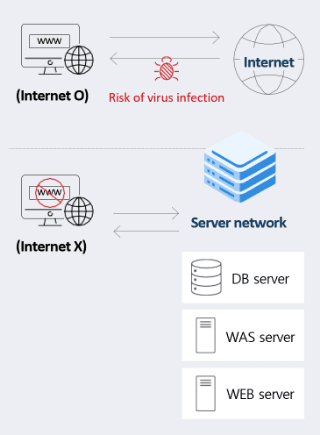
Idea of network separation
Third, application security
Common websites in the form of applications and mobile applications are used by a wide audience, which makes them vulnerable to quick and easy exposure to malicious code. Attacks using application vulnerabilities are occurring even at this very moment. To address these issues, enhance application security, and mitigate the spread of malicious code, the privilege bypass feature is currently under development and undergoing testing. Also, developers must carefully consider the application security types, including authentication, authorization, and encryption, when developing applications and safety through source security verification and mock hacking after completing the app development.
[Wait!] Why authentication and authorization management are more important in the cloud environment
Since cloud environments provide shared resources, special attention must be paid to authentication and authorization management to make sure that users can only access data of which they have proper authorization. Additionally, fully encrypted transmission must be ensured for cloud-based application data communicating over the Internet.
Conclusion: There are three important factors of data center security, the three Ps (people, process, and product).
The progress in security technology paradoxically indicates the emergence of novel forms of attack techniques. In other words, the new security technologies come from counterattacks. The following three P’s are very important to the data centers constantly exposed to hacking threats: People, Process, and Product.
People
The key to data center security is people. The personnel here includes not only security administrators but also infrastructure operators of servers and networks. For security personnel to perform their duties properly, it is essential to understand the importance of security and communicate about technical connections. It is obvious that technology alone cannot maintain security. This is why we invest time and money to educate human resources and train our employees. The continued interest of the decision maker is also crucial to keeping security.
Process
The evolving security threats, growing in sophistication, have created an environment where defense cannot rely solely on technology and solutions. Hackers will try to find and penetrate gaps the security team missed with their advanced techniques, and this is when the process reinforcement is needed. Only then can we detect gaps that technology alone cannot close or proactively defend against.
Product
To create a safe product, security is a critical factor that should not be overlooked from the beginning to the end of development. As with software tests, security must be considered from the beginning of the development life cycle, and code security flaws detected during the development must be addressed to ensure the product's reliability.
[Wait!] The Samsung SDS data center keeps the three principles for airtight security.
The Samsung SDS data center security has three principles: “Don’t let it enter,” “If it's already entered, don’t let it get away,” and “If left, make it useless.”
To this end, Samsung SDS reinforces security by educating people, stipulating processes, and verifying products. Since data centers are where important corporate information is concentrated, they are not always free from unpredictable threats. To keep data centers safe, careful preparation and defense are required at all times.
- Haeyong Yang / Samsung SDS
- Haeyong Yang has performed security tasks in various fields for 19 years, including security planning, cloud security, security breach investigation, physical security, and security consulting. Moreover, he translated six security books into English, such as The Art of Software Security Assessment and Threat Modeling published by Acorn Publisher.
- Seyoung Kim / Samsung SDS
- Seyoung Kim has worked on data center/cloud security policy establishment, architecture security review, and vulnerability check and developed her experience in security diagnosis.