Validated for the Highest Level of Security
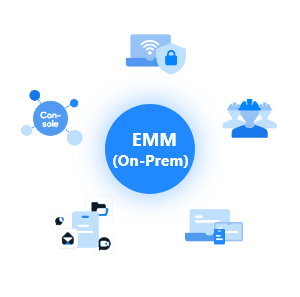
Certified by global certification agencies, our EMM caters to organizations demanding the highest security standards. It meets our customers’ needs with enhanced security features, including App Tunnel and dual VPN chaining
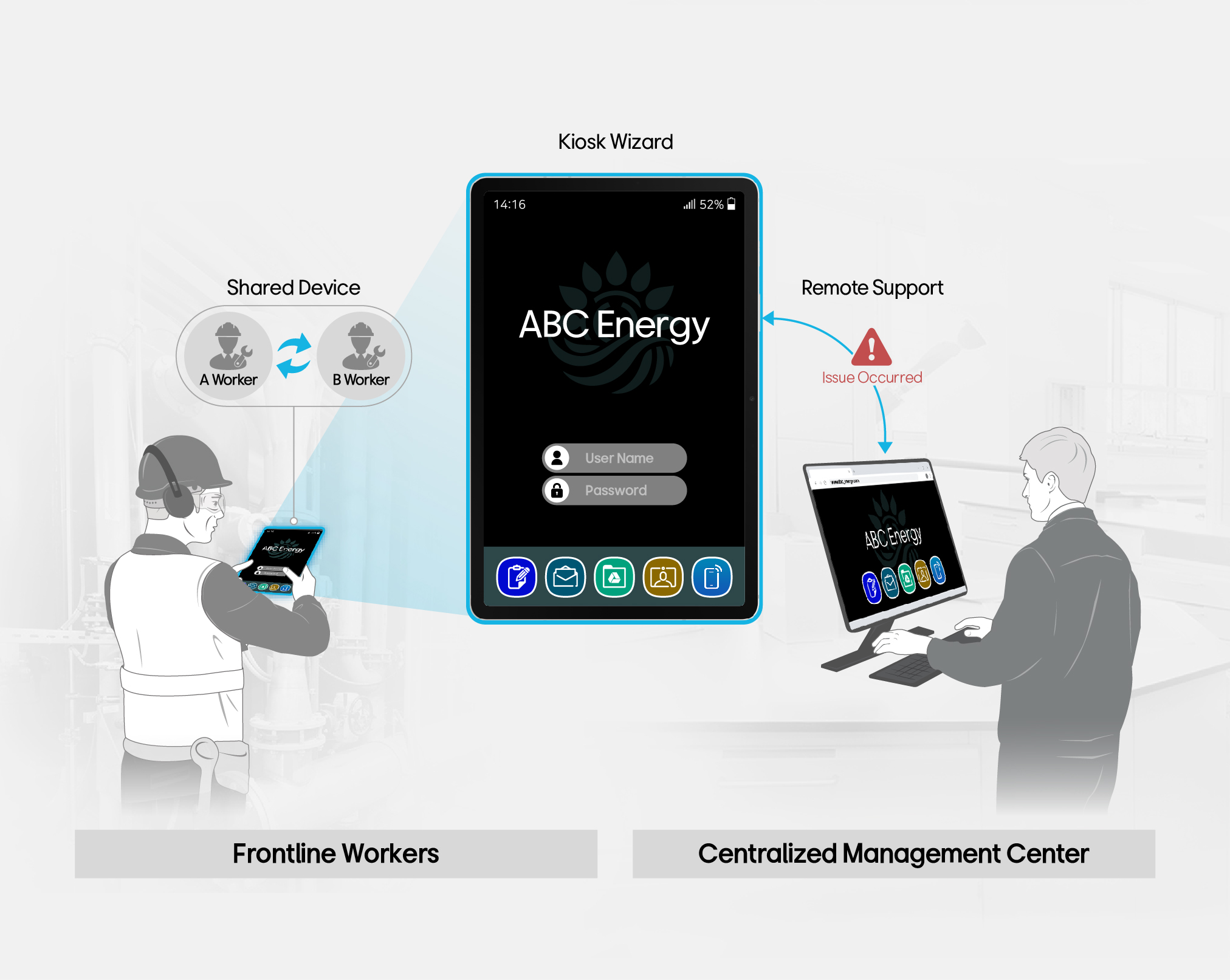
Advanced Features to
Empower your Frontline Workers
Empower your frontline workers with advanced features like Kiosk Mode, Remote Support, and Shared Device Mode
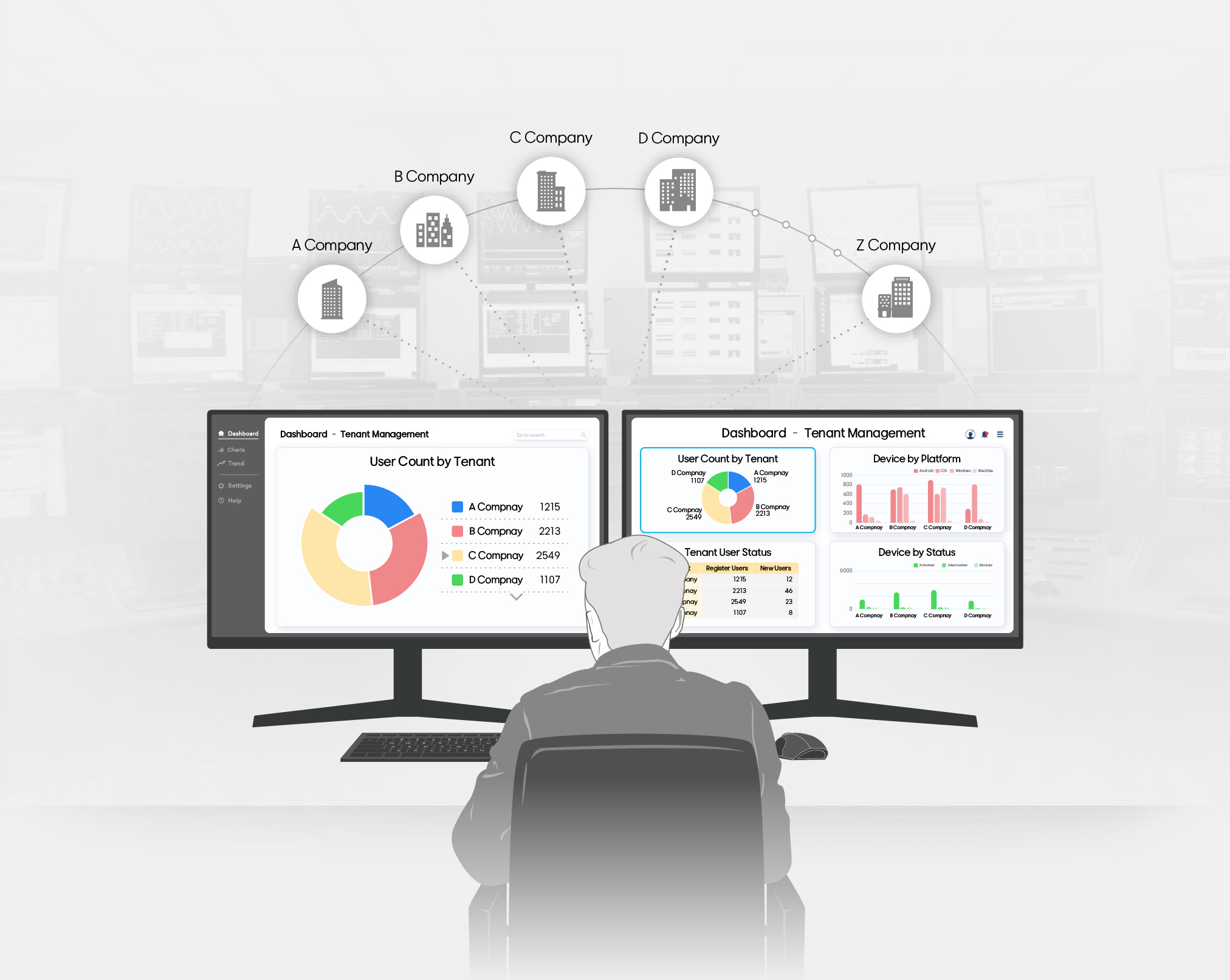
Comprehensive Device Support
across the OS platforms
Provide extensive and adaptable support for a broad spectrum of devices including Android, iOS, and Windows to ensure smooth management
Effortless
Mobile App Management
Efficiently supply and distribute business mobile applications, control access and authority, and monitor usage
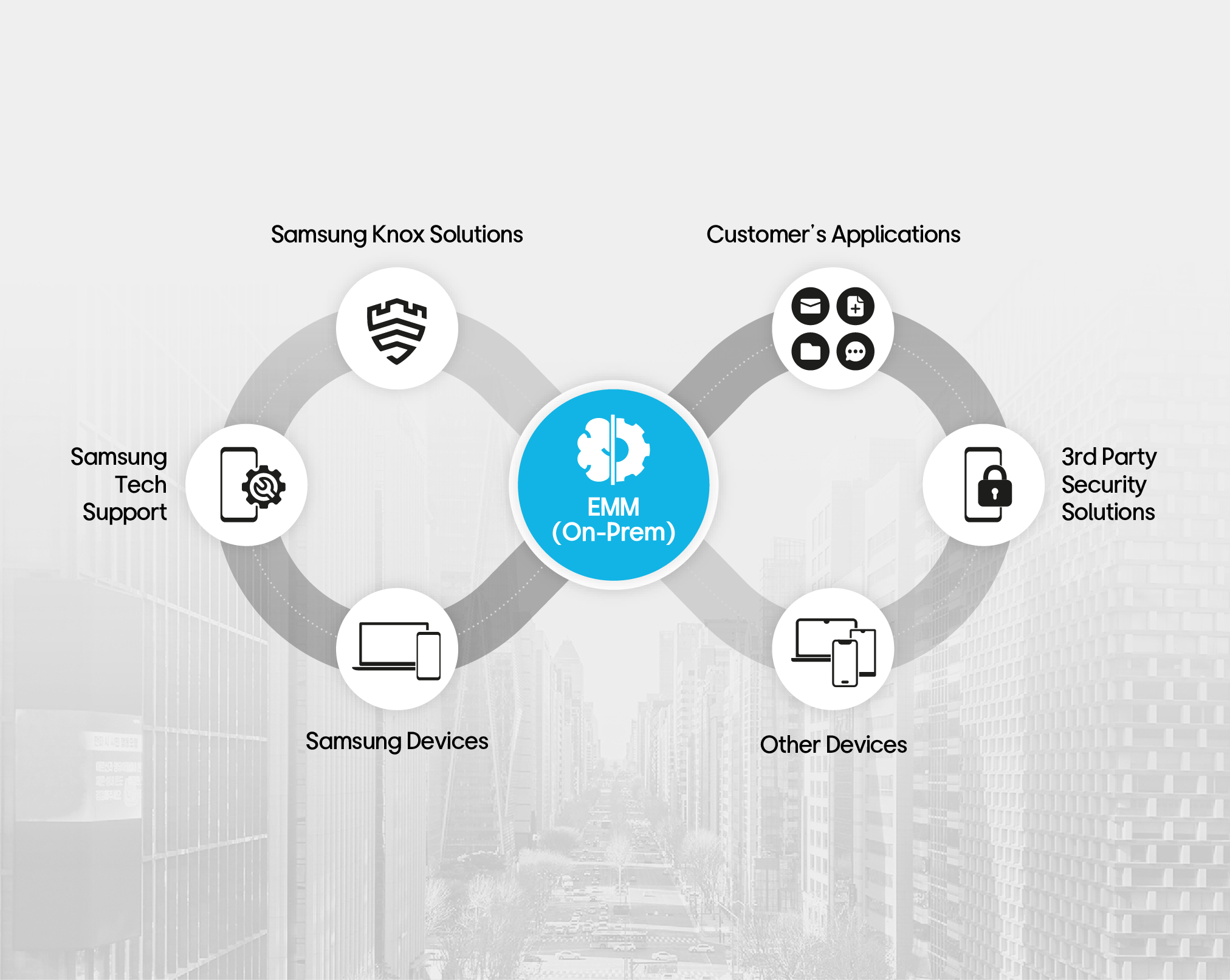
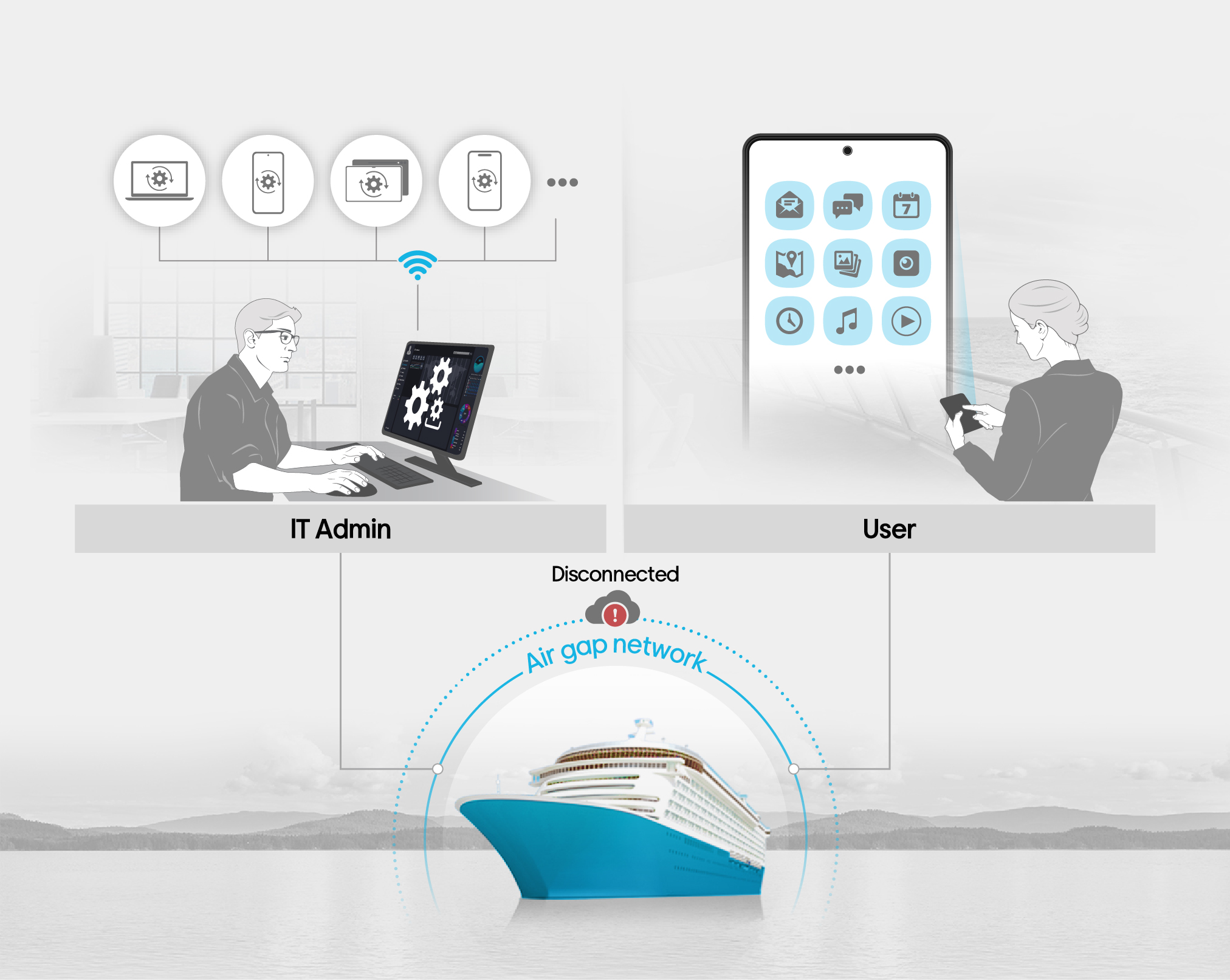
IT Orchestration with Samsung
Devices and Knox Solutions
Through optimized IT orchestration, integrate with various 3rd party solutions seamlessly, including Samsung devices and Knox solutions