[Technology Toolkit]
It is Important to Prevent Security Risks from Development Phase! Trust CAFA+ to Do the Job


Technology Toolkit 2021 is a technical white paper describing core technologies that
are being researched and developed by Samsung SDS R&D Center. We would like to introduce in this paper a total of
seven technologies concerning AI, Blockchain, Cloud, and Security with details on their technical definition, key
features, differentiating points, and use cases to give our readers some insights into our work.
CAFA+(Code Analyzer for ABAP & HANA Plus)
1. Introduction to Technology
Technology Trends and Background
With the arrival of 4th industrial revolution era and digital transformation becoming a necessity rather than a
choice for organizations and businesses, non-face-to-face work environment is expanding more than ever, especially so
with Covid 19 pandemic. Moreover, as the digital transformation accelerates, life without IT is now unimaginable, but
unfortunately it has led to higher security risks and more cyber-crimes with hackers exploiting this opportunity to
launch cyber-attacks. Most of security vulnerabilities occur during the application development phase in other word,
coding, so the best way to prevent security risks would be to pay close attention from design and development
phase.
However, in today’s market wherein product lifespan is becoming shorter and the resulting burden on product
development and cost is growing, companies can easily neglect security issues. As a result, the need has become
greater for automated DevSecOps (DevOps+Security) technology that allows developers to identify and remove security
bugs in development phase. If security bug analysis and removal tool can be incorporated and automated in development
operation cycle, it will free up developers to better focus their attention on product development itself and in the
end, increase productivity and save a lot of money on troubleshooting. Nowadays, it's easy to find global leading
companies that are either adopting or internalizing such tool for their infrastructure due to these beneficial
reasons.
We have been using our very own security bug detection tool – a tool that we built using program semantic
analysis technology - for our Java program inspections for several years. Since 2020, we have added the language
support for ABAP, a de facto programming language in ERP projects, and integrated it into CAFA+, the Samsung
SDS’s standard code inspection tool for ABAP, to enable inspection for code quality and security weaknesses in a
single tool.
Definition
The security bug inspection feature offered by CAFA+ incorporates Abstract Interpretation technology, a
representative static analysis technique that analyzes codes without executing a program. In particular, Taint
Analysis built on top of Abstract Interpretation allows us to infer data inflow path by analyzing data flow. This
allows us to detect data from unreliable source such as values entered by an arbitrary user so that we could prevent
them from penetrating into sensitive areas like SQL execution statements and be exploited by an attacker. Security
vulnerabilities such as XSS, SQL Injection, and Path Traversal all are of the same type and our Taint Analysis
function allows us to perform error-free inspection that is unmatchable to simple syntax pattern inspection of the
past. CAFA+ further enhances the accuracy of detection by leveraging Variable Analysis in predicting the range of
variable values and presence of constants, and using the findings in areas such as conditional branch statements
analysis.
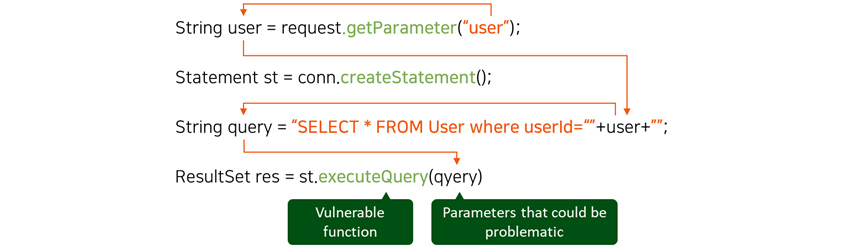
String user =request.getParameter('user'); Statement st = conn.createStatement(); String query ='SELECT*FROM User where userId='+user+''; ResultSet res = st.executeQuery(qyery) - executeQuery: Vulnerable funcion - (qyery): Parameters that could be problematic
2. Key Features
CAFA+ is ABAP code quality and security vulnerability inspection tool that’s built upon our 15 years of
know-hows for ERP development and operation. We have continued to build a robust security response system, reacting
quickly to changes in SAP ABAP technology environment.
Supports new technology environment (S/4HANA, ABAP 7.5)
Our technology supports new HANA DB environment and the latest ABAP 7.5 syntax. It automatically identifies codes
that need to be modified for migration to HANA DB and accurately analyzes security bugs written in new ABAP 7.5
syntax.
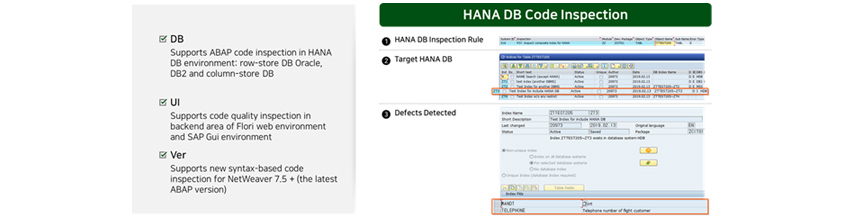
DB : Supports ABAP code inspection in HANA DB environment: row-store DB Oracle, DB2 and column-store DB UI : Supports code quality inspection in backend area of Flore web environment and SAP GUI environment Ver : Supports new syntax-based code inspection for NetWeaver 7.5 plus (the latest ABAP version)
HANA DB Code inspeciton1. HANA DB Inspection Rule, 2. Target HANA DB, 3. Defect Derected
Supports ABAP development quality and performance check
Our CAFA+ provides about 150 code inspection rules and this number keeps on growing thanks to years of our ERP
operation know-hows. These inspection rules allow us to provide our developers with support that they need to ensure
safe and quality coding. These rules are used to 1) check for developers’ compliance with basic development
standards, 2) address design issues like low maintainability resulting from high code complexity or improper
modularization, 3) handle performance degradation issues like codes that have the potential to be executed
indefinitely or expensive statements that are repeatedly executed, and 4) inspect abnormal termination issues like
uncaught exceptions.
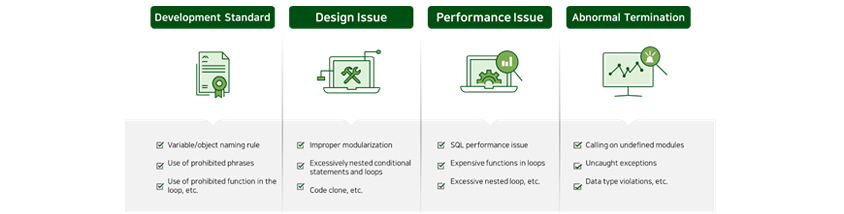
- Variable/object naming rule
- Use of prohibited phrases
- Use of prohibited function in the loop. etc
- improper modularization
- Exessive nestedconditonal statemants and loops
- Code clone, etc
- SQL performance issue
- Expersive function in loops
- Excessive nested loop, etc
- Calling on undefined modules
- Uncaught exceptions
- Data type violations, etc
Supports ABAP security defect inspection
We’ve listened to the voices of our on-site developers for a year concerning issues such as authentication
bypass, incorrect password use, and SQL statement injection and we used the findings towards our handling of security
defects that are occurring frequently and have high impact. We go beyond of just providing simple result to our
developers but provide easy-to-understand explanations and specific examples of counter-measures we took,
subsequently, minimizing the time and efforts that they put into their work and still enhance their work quality.
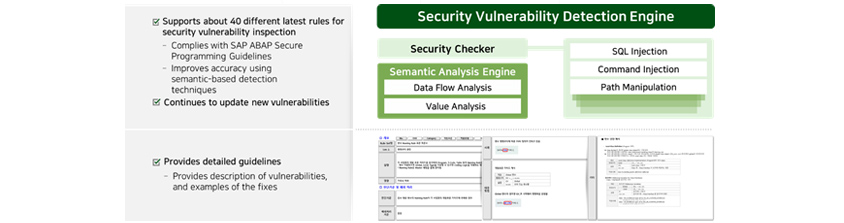
- Supports about 40 different latest rules for security vulnerability inspection
- Complies with SAP ABAP Secure Programming Guidelines
- Improves accuracy using semantic-based detection techniques
- Provides detailed guidelines
- Provides description of vulnerabilites and examples of the fixes
- Security Checker
- SQL injection, Command Injection, Path Manipulation
- Semantic Analysis Engine
- Data Flow Analysis, Value Analysis
3. Differentiating Points
As shown below, CAFA+ offers our customers more varied functions than the default code inspection function offered in
SAP platform.
First, our tool provides about 150 code inspection rules and security vulnerability inspection function currently
applied in development and operation of ERP for Samsung Group. It enables to us to improve customers’ code
security and reinforce maintenance & repair process with inspection rules that have been refined with years of our
on-site experience.
Second, our tool scores individual inspection result and provides a quantified comprehensive quality index. Unlike
most of other tools that only provides item-by-item compliance status, CAFA+ provides quantified result in single
quality index that’s useful in setting quality gate standard.
Third, our tool can customize inspection items and action policies to meet the needs of organizations and projects at
hand. Most CAFA+ functions can be configured through SAP GUI environment familiar to ABAP developers, and
administrators are free to establish policies according to the needs, quality requirement, and on-site situation of
each project and thus boost the efficiency of project.
Fourth, developers can easily use the tool at any time with simple manipulation of menu items without leaving SAP
environment. The tool allows developers to check for issues every time they code a function or save a file and as a
result, they can acquire safe coding habit in no time.
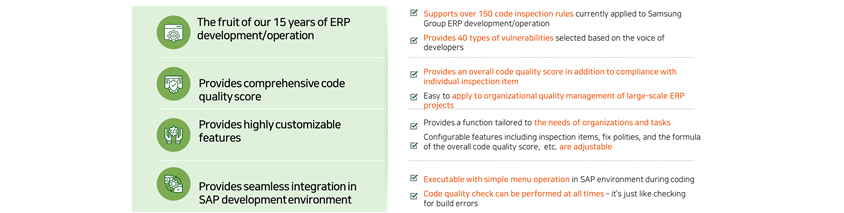
- Thee fruit of out 15 years of ERP development/operation
- Supports over 150 code inspection rules currently applied to Samsung Group ERP development/operaiton
- Provides 40 types of vulnerablilities selected based on the voice of developers
- Provieds comprehensive code quality score
- provides an overall code quality score in addtion to compliance with individual inspection item
- Easy to apply to organiaztional quality management of large-scale ERP projects
- Provides hightly custiomizable features
- Provides a function tailor to the nees fo organizations and tasks
- Configurable feathures including inspection items, fic polites, and the formula of the overall code quality score, etc. are adjustable
- Provides Seamless integration in SAP developement environment
- Executable with simple menu operation in SAP environment during coding
- Code quality check can be performed at all times - it's just like checing
4. Use Case
We can use CAFA+ not only as a development security tool for SAP development projects but also as an operational
security tool for operation projects. Because it can be executed with just a few click of a button without having to
leave SAP environment, CAFA+ provides real-time quality enhancement environment where a coding developer or inspecting
operator can perform quality and security inspection using one-stop process. This helps to eliminate all the
inspection processes that are not needed thereby shortening inspection time and improving productivity in general.
Moreover, integrated batch inspection (weekly, monthly) function allows QAO and security personnel to automatically
perform full inspection of SW quality and security, leading to an improvement in work efficiency and quality
standard.

- Use Case 1: Code quality inspention in development stage
- Developer performs self-inspection and addresses issues in real time during coding
- QnA or Security personnel conducts inspection periodically upon code integration(perovides batch processing funcion)
- Use Case 2: Code quality inspection in operation stage
- performs inspection of code changes made to the deployed system
- QnA or Security personnel conducts inspection periodically(e.g. batch processing) according to ERP system's inspection cycle
- Real-time inspection during Development Stage
- Developer
- Self-inspection of codes developed/modified by developer
- Fullintegrated inspection
- QAO,Security Personnel
- SAP DB Server(Source Code), Inspeciton Report
- Weekly/Monthly Full inspection, Provides inspection result report
5. Closing
We implemented a methodology that reflects code inspection and tuning from the point when we first launched ERP
business. We built our own CAFA+ that supports the latest ABAP syntax and HANA DB environment to allow us to quickly
respond to changes in SAP technology environment. There are many individual tools that are applicable to areas such as
security vulnerability check, program structure analysis, program performance prediction, and program maturity index
measurement, but CAFA+ is the only integrated ABAP inspection platform that is capable of performing all these
functions at once.
The work that remains to be done is detecting security defects in programs written in multiple languages. An example
would be identifying potential threat where an unidentified attack code introduced in JavaScript frontend may flow
into sensitive function after it goes to ABAP backend. If we can build a technology that can link and analyze programs
written in different languages, we can inspect everything from SAP’s new frontend environment, JavaScript-based
Fiori to backend ABAP program as a single context and detect hidden security vulnerabilities more accurately.
# References
[1] Gartner, “DevSecOps: How to Seamlessly Integrate Security Into DevOps”
[2] Capers Jones, Applied Software Measurements, McGraw-Hill, 1996-2008
▶ The content is proected by law and the copyright belongs to the author.
▶ The content is prohibited to copy or quote without the author's permission.
- The First Step to Smart Textual Analysis, KoreALBERT
- Smart QA Model That Understands Even Complex Tables
- I Will Give You Data, Label It~ Auto Labeling!
- The Connecting Link for Everything in the World, It’s in the Knowledge Graph
- Easy and Simple Blockchain Management, Nexledger!
- No More Short of GPU!
- In the Age of When Customer Data Must Be Treated as a King, PET Will Take on the Responsibility
- It is Important to Prevent Security Risks from Development Phase! Trust CAFA+ to Do the Job

SW Security Team at Samsung SDS R&D Center
As SW security expert at Samsung SDS, he is involved in malicious code detection and counter-attack technology and automated program analysis technology for security bug detection.
If you have any inquiries, comments, or ideas for improvement concerning technologies introduced in Technology Toolkit 2021, please contact us at techtoolkit@samsung.com.
-
[Technology Toolkit]
In the Age of When Customer Data Must Be Treated as a King, PET Will Take on the Responsibility - Effective Personal Information Protection Technology for Post COVID-19 Era
- Samsung SDS America showcases Nexsign at Finovate Spring 2018
- Bridging the gap between user experience and mobile security
- The importance of secure browsers in commercial banking