Setting the Standard for Security in the Post-Quantum Era!
Samsung SDS's Security Technology Recognized by NIST and KpqC


Key Points Summary
- World-Class Security Research Expertise - The Samsung SDS’s Security Research Team has recently been invited to deliver presentations at all four workshops hosted by NIST, the most authoritative organization in the field of cryptographic standards.
- Proactive Research for the Post-Quantum Era - As quantum computing threatens to undermine existing cryptographic systems, Samsung SDS is actively participating as a key player in the U.S. NIST standardization project, driving proactive standardization efforts.
- Impact-Driven Research Philosophy - Embracing the philosophy that a select group of talented individuals can change the world, the team focuses on future technology research alongside indispensable experts in their respective fields.
We had the privilege of meeting Ji-hoon Cho, a team leader leading the Security Research Team at Samsung SDS. With a background in cryptography from the University of Waterloo in Canada and a Ph.D. from the UK, Ji-hoon Cho joined Samsung SDS, where he drives the development of next-generation security technologies, including White-Box Cryptography and Post-Quantum Cryptography.
Recently, he has continued to expand his global influence by delivering technical presentations at NIST workshops for four consecutive years. Now, let us introduce you to the future of security as envisioned by the Security Research Team Leader at Samsung SDS.
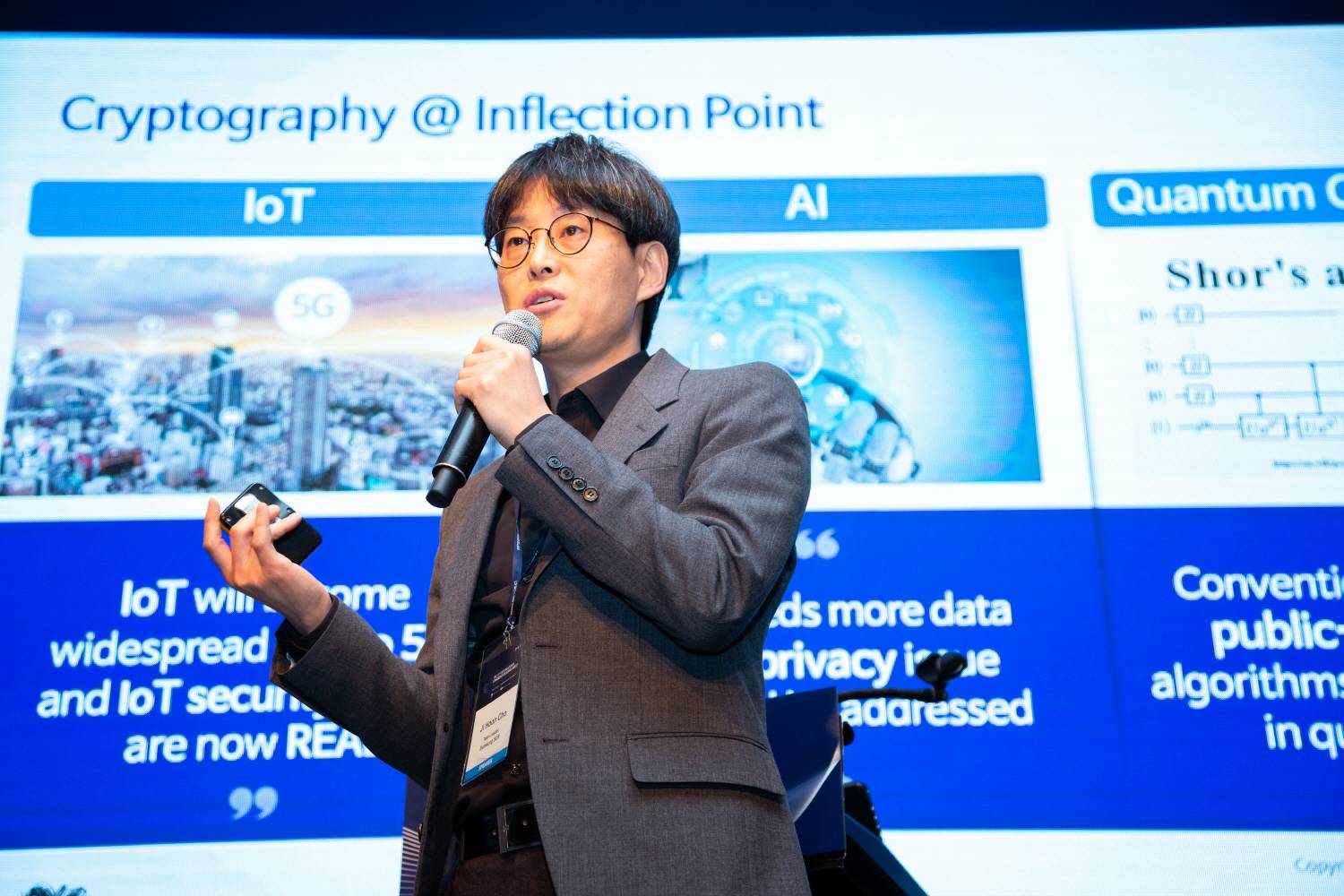 Ji-hoon Cho is delivering a presentation titled ‘Cryptography at a Turning Point’.
Ji-hoon Cho is delivering a presentation titled ‘Cryptography at a Turning Point’.
“The two pillars of the Security Research Team: Security Algorithm Lab and SW Security Lab”
How did you first become involved in the field of cryptography?
I didn’t have a strong resolve for cryptography from the start. While majoring in mathematics at university, I was at a crossroads, debating whether to continue with mathematical research or explore another field. During this time, I applied to several graduate schools and was accepted.
The deciding factor for choosing the University of Waterloo was an advice from a close senior alumnus. He said, “Cryptography is currently the most popular field for mathematicians. If you’re interested in cryptography, you should go to Waterloo, the best university in the field of cryptography.” Looking back, it was a time when cryptographic research was just beginning to take off in Korea, and this shift in academia seemed to have been reflected in the senior alumnus’s advice.
What is the structure of the Samsung SDS’s Security Research Team, and what are the main areas of research?
The Samsung SDS’s Security Research Team consists of two Labs. The Security Algorithm Lab focuses on quantum-resistant cryptography and privacy-preserving technologies to prepare for the era of quantum computing. Meanwhile, the SW Security Lab conducts research on security vulnerability analysis and is working on the software test automation project.
In light of the recent surge in security incidents, I’ve become even more convinced of the importance of this field. Most hacking incidents exploit vulnerabilities hidden within software. Therefore, the philosophy of the SW Security Lab is to “eliminate potential entry points for attackers before they can exploit them.” Instead of relying on post-incident response, we emphasize proactive prevention, blocking vulnerabilities at their source from the software development stage itself.
 Ji-hoon Cho giving an interview
Ji-hoon Cho giving an interview
“Two consecutive wins at SBFT world championship”
We heard you also achieved success at the prestigious software testing competition, SBFT.
Testing is a cornerstone of software development. Bill Gates once emphasized its importance, stating, "We have as many testers as developers. Testers dedicate all their time to testing, and developers spend half their time on it." Testing is indeed that important. However, to reduce software development costs, it’s essential to identify errors early on. If issues are discovered during the QA phase, it becomes more expensive. To address this, Samsung SDS’s Security Research Team has developed an innovative automatic unit test generation technology that allows developers to perform unit tests while writing code.
Leveraging this technology, we entered the SBFT international competition—a premier event where top research teams in software engineering compete globally. Our Security Research Team participated in the Java category, a language widely used in enterprise environments, and secured two consecutive victories in 2024 and 2025. Notably, we outperformed renowned teams such as JetBrains, the creator of Kotlin for Android phone, and MIT’s research team, marking a significant achievement in the field.
What is SBFT Competition?
The SBFT (Search-Based and Fuzz Testing) Competitionis an integral part of the SBFT Workshop, which explores latest research in software testing automation. The workshop is co-located with ICSE (International Conference on Software Engineering), one of the premier conferences in the field of software engineering. The SBFT Workshop offers a dynamic platform for researchers and practitioners to share and discuss advancements in testing technologies, featuring diverse activities such as research presentations, keynote speeches, and a tool competition.
What is Automated Unit Test Generation Technology?
Automated Unit Test Generation Technology is a method that analyzes software code written by developers to automatically create test code that verifies the functionality and stability of the application. Essentially, it generates additional code to automatically identify potential bugs within the original code. But, why does the Security Research Team focus on detecting bugs?
The primary reason is that the most critical bugs are those that can be exploited by hackers, known as security vulnerabilities. In traditional software development, developers manually wrote these test codes, which prolonged development time and resulted in inconsistent test code quality based on individual expertise. By leveraging Automated Unit Test Generation Technology, high-quality test cases can be automatically produced by analyzing the original code, accounting for major execution paths and exceptional scenarios.
“A safe with an untraceable key: White-Box Cryptography”
We heard that the ‘White-Box’ technology, which you first researched and developed at Samsung SDS, is now being utilized in various Samsung products. What exactly is this technology?
To explain White-Box Cryptography, it’s essential to first understand the limitations of traditional encryption methods. Every software contains numerous sensitive pieces of information—such as user data, authentication details, and payment information—that must never be exposed externally.
To protect this data, encryption is employed. However, traditional methods have a critical flaw: the existence of a key. It’s akin to placing valuable items in a safe and leaving the key right next to it. Since the encrypted data and the decryption key coexist within the same system, hackers can compromise everything if they manage to locate the key.
From this perspective, the idea behind White-Box Cryptography emerged: “What if we make it impossible to find the encryption key itself?” The technology we developed creates a safe where finding the key is fundamentally impossible - essentially, a safe without a key.
To turn this innovative idea into reality, we collaborated strategically with cryptography experts Professor Orr Dunkelman and Professor Nathan Keller from Israel. Our goal was to implement a secure yet fast encryption algorithm. The results exceeded expectations.
Today, this technology is recognized as an essential tool in the rapidly growing defense sector and is widely applied across various Samsung solutions and SCP Cloud. It brings me a profound sense of fulfillment to know that it contributes to strengthening the core infrastructure of future industries.
What is White-Box Cryptography?
White-Box Cryptography is a security technology designed to protect secret keys and cryptographic algorithms even when the internal environment where the cryptographic algorithm is executed is assumed to be fully exposed. White-Box Cryptography obfuscates the cryptographic algorithm and key, applying various transformation techniques to prevent attackers from extracting critical information.
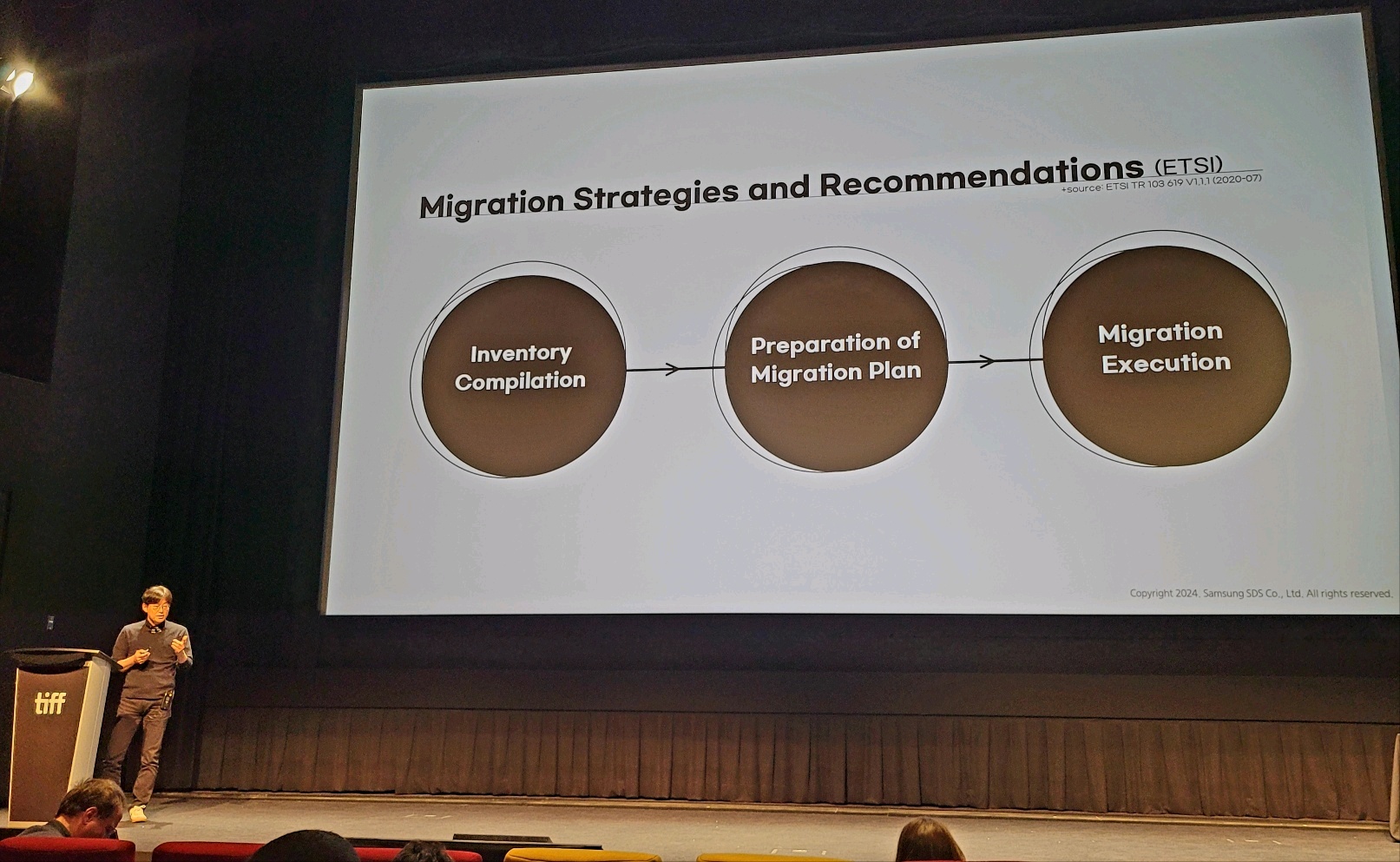 Ji-hoon Cho presenting cryptographic transition technologies at the Real World Crypto 2024, the premier conference in the field of industrial cryptography
Ji-hoon Cho presenting cryptographic transition technologies at the Real World Crypto 2024, the premier conference in the field of industrial cryptography
“The first cryptographic revolution since 1976”
Lately, cryptography is said to be in a transition period toward ‘Post-Quantum Cryptography’. Why is this so important and challenging?
To answer this question, we first need to understand the historical turning point of 1976. That year marked the introduction of public-key cryptography, which provides user authentication and data tamper detection.
This technology has become the essential foundation for building trust across the entire internet. Without public-key cryptography, the internet might still be a limited tool used only for defense and specific professional fields.
What’s remarkable is that since 1976, there has never been a complete replacement of public-key cryptography. For nearly 50 years, we’ve relied on the same technology. During this time, IT systems have become unimaginably complex. Comparing the digital environment then and now is like comparing a bicycle to a spaceship.
"How can we safely replace the widespread public-key cryptographic systems across the global internet infrastructure with minimal cost and time?" This is a challenge humanity has never faced before. If we had infinite time and resources, it might be possible, but reality is different. Since public-key cryptography has been deeply embedded in all internet systems, this task can be described as a historic transformation that determines the survival of digital civilization.
Recognizing the gravity of this issue, the U.S. NSA (National Security Agency) and the White House entrusted this difficult project to NIST. They were tasked with finding a comprehensive answer to questions like: "What methodologies are needed? What technologies are required? How should they be standardized?"
What is NIST?
NIST (National Institute of Standards and Technology) is a federal agency under the U.S. Department of Commerce, established in 1901. Its mission is to develop and promote standards in science and technology, driving innovation and enhancing quality across various industries. NIST has been a global leader in creating influential guidelines, particularly in the Cybersecurity Framework (CSF), the Zero Trust security model, and Post-Quantum Cryptography (PQC). These standards are widely recognized and trusted internationally as reliable benchmarks for compliance and best practices.
We heard that Samsung SDS’s Security Research Team is also participating in the Post-Quantum Cryptography (PQC) transition project led by the U.S. NIST.
Yes, that’s right. In November 2021, we discovered the PQC transition project being conducted by NIST. It was a collaborative proposal format where companies could apply, but many were skeptical. Even though NIST security standards are widely used globally, there was a perception that they primarily collaborate with U.S. companies, raising questions like, "Would they include a Korean company?"
However, I thought, "Let’s give it a try. There’s nothing to lose," and decided to apply for it myself. To my surprise, I received an invitation for an interview. After about a month or two without hearing back, I assumed it wasn’t going to happen. But then, two months later, I got a call for an interview, and two months after that, I received the message, "Let’s work together."
As a result, Samsung SDS was selected for the first time to collaborate with global companies like AWS, Microsoft, and IBM. Since then, Samsung SDS has continued to participate as a key author in the project, contributing to the development of the standard documents.
 The official website of NIST
The official website of NIST
How did Samsung SDS manage to join such a major U.S. project? We are curious about the secret behind it.
Initially, we lacked the specific technologies related to the project. Therefore, during the interview, we emphasized not only our team’s theoretical research capabilities in various cryptographic technologies but also our extensive practical implementation experience. We highlighted that Samsung SDS Research has not only designed cryptographic algorithms but has significant experience in deploying cryptographic algorithms across diverse real-world environments.
This is known as cryptographic engineering in professional terminology and our team had over 15 years of expertise in this field. The combination of theoretical knowledge and practical experience set us apart from typical university research labs. As a result, Samsung SDS was recognized as a key contributor to the NIST project and has continued to actively participate in it to this day.
“We also support the journey of Korea Post-Quantum Cryptography”
Recently, you’ve been contributing to the standardization of quantum-resistant cryptography through the KpqC (Korea Post-Quantum Cryptography) competition, which is sponsored by South Korea’s National Intelligence Service (NIS).
Over the past three years, the NIS-sponsored KpqC competition has been held to develop quantum-resistant cryptography for Korea. The competition was conducted in two areas: digital signatures and key exchange. In the digital signature category, Samsung SDS’s Security Research Team secured first place.
The reason we were able to achieve such remarkable results in less than three years is that we took a different approach from conventional methods. Traditional quantum-resistant cryptography is based on complex mathematical problems, which carry the risk of being solved by a genius at any time. To address this, we proposed a novel method for designing public-key cryptography without relying on such difficult mathematical problems. This innovative approach was one of the key reasons we were selected in this competition.
 The Quantum-Resistant Cryptography Research Group leading PQC research and development in Korea
The Quantum-Resistant Cryptography Research Group leading PQC research and development in Korea
This achievement was made possible in part due to our collaboration with KAIST, where a senior alumnus from my time studying cryptography at the University of Waterloo is affiliated. Through this industry-academia partnership, we were able to provide Ph.D. students with meaningful and positive experiences about Samsung SDS Research. They came to recognize that "At Samsung SDS Research, we engage in profound research to tackle complex challenges in the field and drive meaningful change in the world." As a result, several students were inspired to join Samsung SDS Research. This experience reinforced the idea that conducting impactful, in-depth research and achieving significant results are ultimately the most effective strategies for attracting top talent.
“We presented two papers at EuroCrypt in one year”
Please tell us about the two papers you recently presented at EuroCrypt.
EuroCrypt is the world’s most prestigious cryptography conference. Having the opportunity to present two papers in a single year at EuroCrypt is a testament to the exceptional caliber of our research team.
The first paper, titled "Relaxed Vector Commitment for Shorter Signatures," introduces foundational technology for quantum-resistant cryptography. It is a critical component in the development of quantum-resistant systems. Among the 14 candidates under consideration for NIST’s quantum-resistant cryptography standardization, six rely on zero-knowledge proofs. However, the problem with this protocol is its inefficiency.
Driven by the question, "Can we improve this inefficiency?" we embarked on a research journey that led to the development of foundational technology that significantly reduces size compared to existing methods while maximizing efficiency. The academic community has taken notice of the transformative potential of this technology, which has been recognized through its publications. Beyond quantum-resistant cryptography, this innovation holds broad applicability across next-generation fields such as blockchain and stablecoins.
The second paper, titled "Making GCM Great Again," was another challenge. It arose from the realization that "We need a new encryption paradigm to meet the demands of the data explosion era." Symmetric-key encryption algorithms currently used for data encryption, were developed in the 1980s and 1990s—long before the need to process vast amounts of data became a reality.
However, the situation has changed. In today’s era of big data, cloud computing, and IoT, we need encryption technologies capable of handling large-scale data. To address this, we developed a mathematical design methodology for safely and efficiently using symmetric-key encryption in modern environments. As I mentioned earlier, NIST has also acknowledged this challenge and is actively working on standardization efforts. We also presented our research findings on this topic at the NIST workshop held in June 2024.
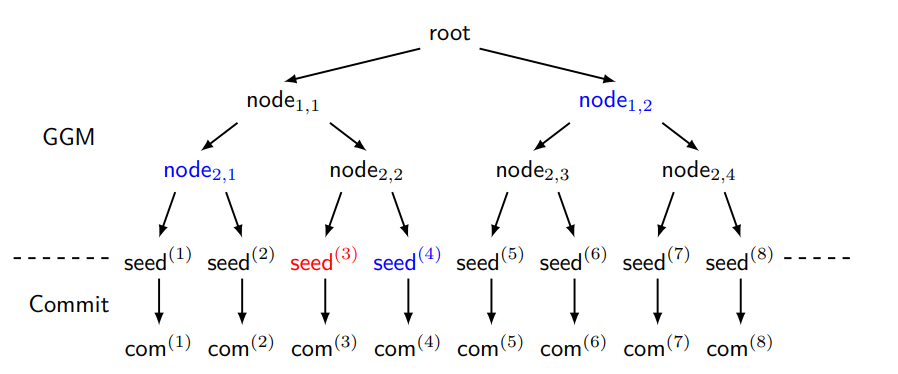 Image included in “Relaxed Vector Commitment for Shorter Signatures” paper
Image included in “Relaxed Vector Commitment for Shorter Signatures” paper
“Together with the UN, we are exploring solutions to shared challenges of humanity”
Lastly, we want to hear about your experience participating in a UN project.
The collaboration between the UN and Samsung SDS is a prime example of how technology can contribute to human welfare. By securely integrating and analyzing data from organizations across different countries, we can develop effective solutions to critical global issues such as preventing child trafficking, addressing poverty, and responding to refugee crises.
However, there is a condition: ensuring data privacy and security, as sensitive data cannot be directly exchanged between nations. To address this, we are working with the UN Statistics Division (UNSD) and statistical office of each country to develop a technology that enables analysis as if all data were integrated, without actually exchanging it.
By leveraging cryptographic techniques, we aim to create a virtual integrated environment that protects each country's data while only sharing the analysis results. This project embodies the vision of "technology contributing to solving humanity's shared problems beyond borders." Every time I participate in such initiatives, I feel a strong sense of mission as a researcher.
“We delve deeply into our work, with a select group of talented individuals”
As the leader of the Security Research Team at Samsung SDS, do you have a particular philosophy?
I strive to stay aligned with evolving paradigms. The pace of technological advancement has accelerated, and the speed at which technology disseminates has also increased, ushering in an era where only the leading technology can survive. Observing these shifts, I’ve become convinced that "corporate research labs must now focus on truly specialized and impactful research." I’ve consistently seen how a small group of talented individuals can create significant impact, reinforcing the importance of carving out a uniquely differentiated domain that only we can achieve.
 Ji-hoon Cho outlining the future of next-generation security technologies
Ji-hoon Cho outlining the future of next-generation security technologies
“Presenting fundamental solutions through 'security by design'”
Lastly, what do you think security means to a company?
Security is a critical risk factor for businesses. The core role of management is to minimize risks while ensuring sustainable operations. However, if security is not managed effectively, everything can be lost in an instant. Particularly in Korea, compared to global companies, there is still a lack of awareness about security risks. But the situation is evolving. Security incidents will become more frequent, and their scale and impact will grow increasingly severe.
As we transition into the AI era, the frequency and severity of security incidents will continue to rise. Geoffrey E. Hinton, a Nobel laureate in physics and often referred to as the ‘father of AI,’ has warned that as AI technology advances, cyberattacks will become more sophisticated and rapid at a lower cost, leading to the proliferation of hacking. In response, he has even distributed his assets across multiple banks. Now is the time for companies to recognize security not as an optional choice but as an essential business strategy, prioritizing it and managing it systematically.
What is Samsung SDS's approach to corporate security?
With over 20 years of experience in the field of security, I’ve come to a key insight: "security must be implemented through systematic and consistent system design." Just as a building can collapse despite strong materials and excellent construction techniques if the design is flawed, security is no different.
Unfortunately, most software companies in Korea are not effectively applying the principle of 'security by design'. Why is this the case? It requires significant time and a substantial number of skilled professionals. While many aspects of software development have been automated, the initial and final stages of security activities—security architecting and penetration testing—remain manual and heavily dependent on the expertise of the personnel involved. To address this challenge, our team is conducting research to automate these processes using AI-based solutions. Our goal is to develop a solution that enables 'security by design' without the need for specialized personnel, leveraging advancements in LLMs and Agentic AI.
“The one strategy to prepare for an unpredictable future”
Lastly, please share your research philosophy or vision for the future.
I set long-term goals, but I focus on the present day. My philosophy is to live each day to the fullest, as if it were my last. That doesn’t mean I live without planning for the future. (Laughs) While I prepare for tomorrow, I also strive to live each day meaningfully, as if it were my last.
This approach is particularly important in the field of R&D. The pace of technological change is so rapid that long-term plans can become a hindrance rather than a help. Innovative technologies can emerge suddenly, requiring immediate changes to strategies. In large organizations like Samsung SDS, adjusting existing plans in response to such changes can be incredibly challenging. It’s like turning a large ship 180 degrees, which takes significant time and energy, unlike a small boat. Especially in IT companies, R&D plans must be flexible and ready to adapt to changes. When such changes are detected, plans must be adjusted immediately without hesitation.
As an executive in a corporate research lab, I sometimes face heavy responsibilities and numerous variables that can make things difficult. However, I approach each day with a sense of mission and excitement, grateful for the opportunity to be at the forefront of change and to pave new paths in the lab.

From White-box cryptography, a safe with an untraceable encryption key, to quantum-resistant cryptography, the future being crafted by Samsung SDS’s Security Research Team transcends mere technological advancement. Amidst the cryptographic transformation—a momentous era unseen since 1976 - we eagerly anticipate the ongoing journey of Samsung SDS’s Security Research Team as they protect our digital civilization at the forefront of this historic challenge. Discover more stories on the Samsung SDS Technology Blog.