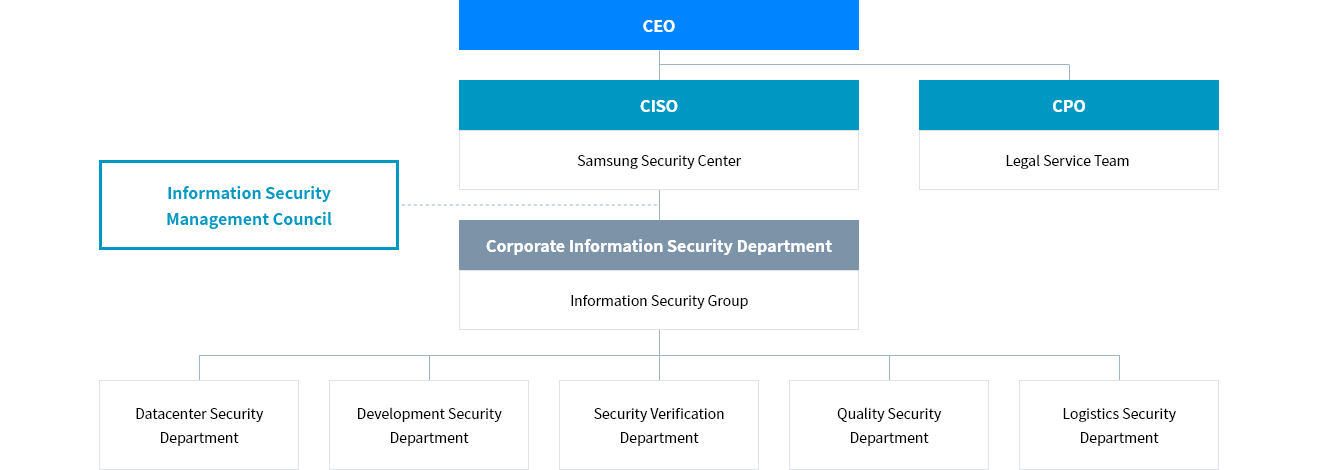
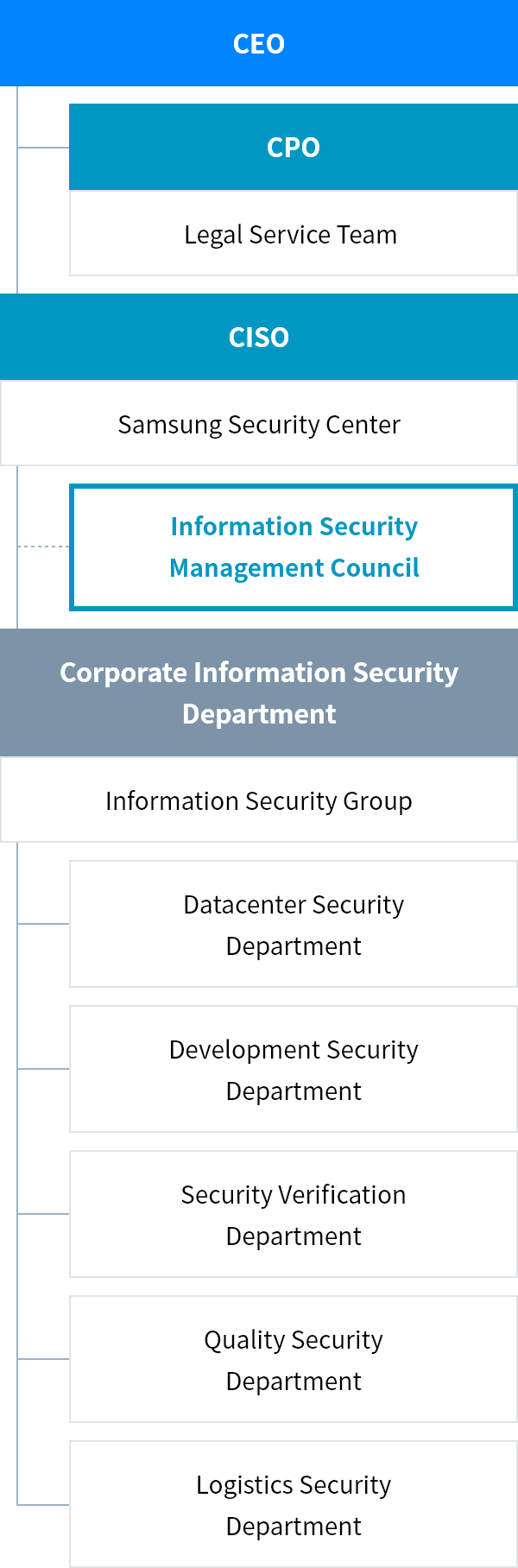
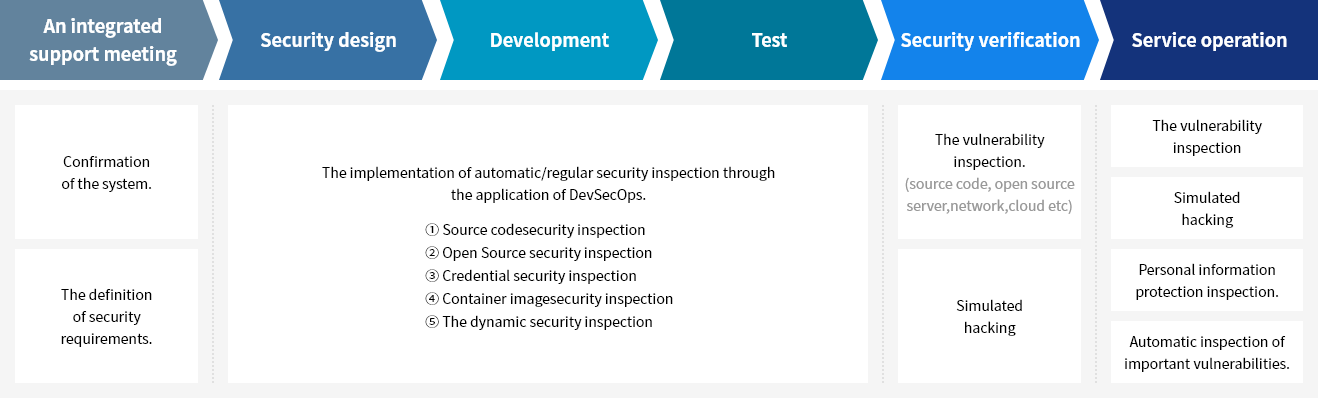
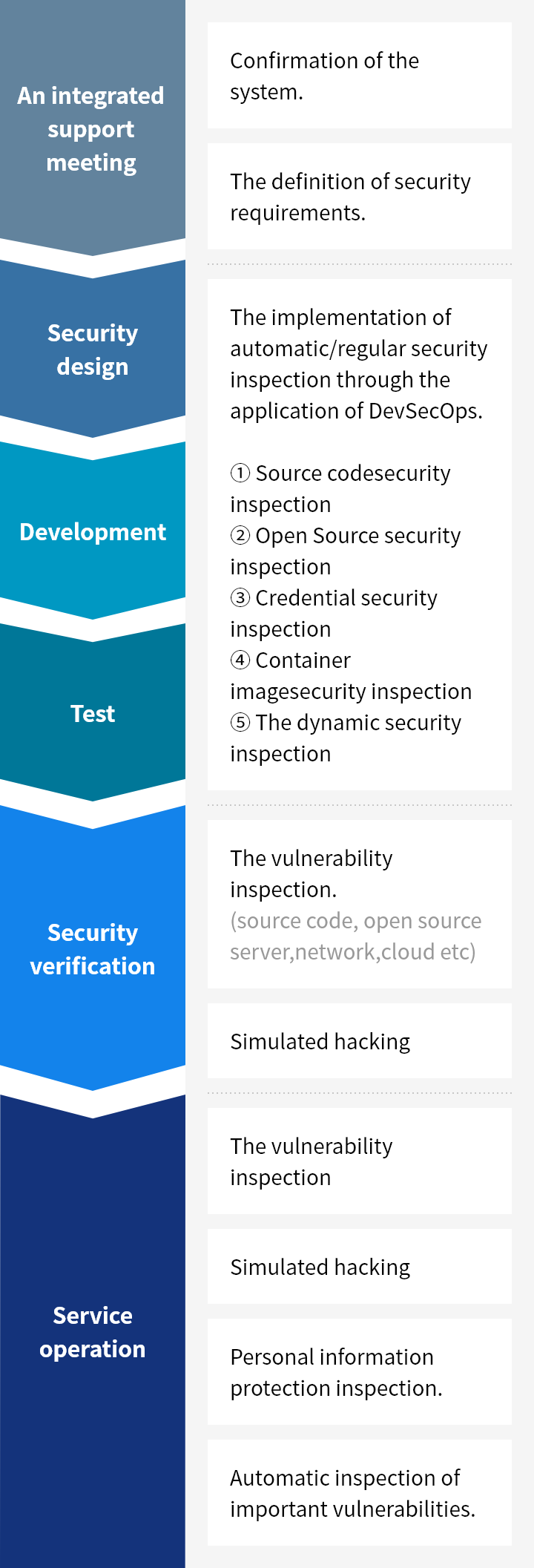
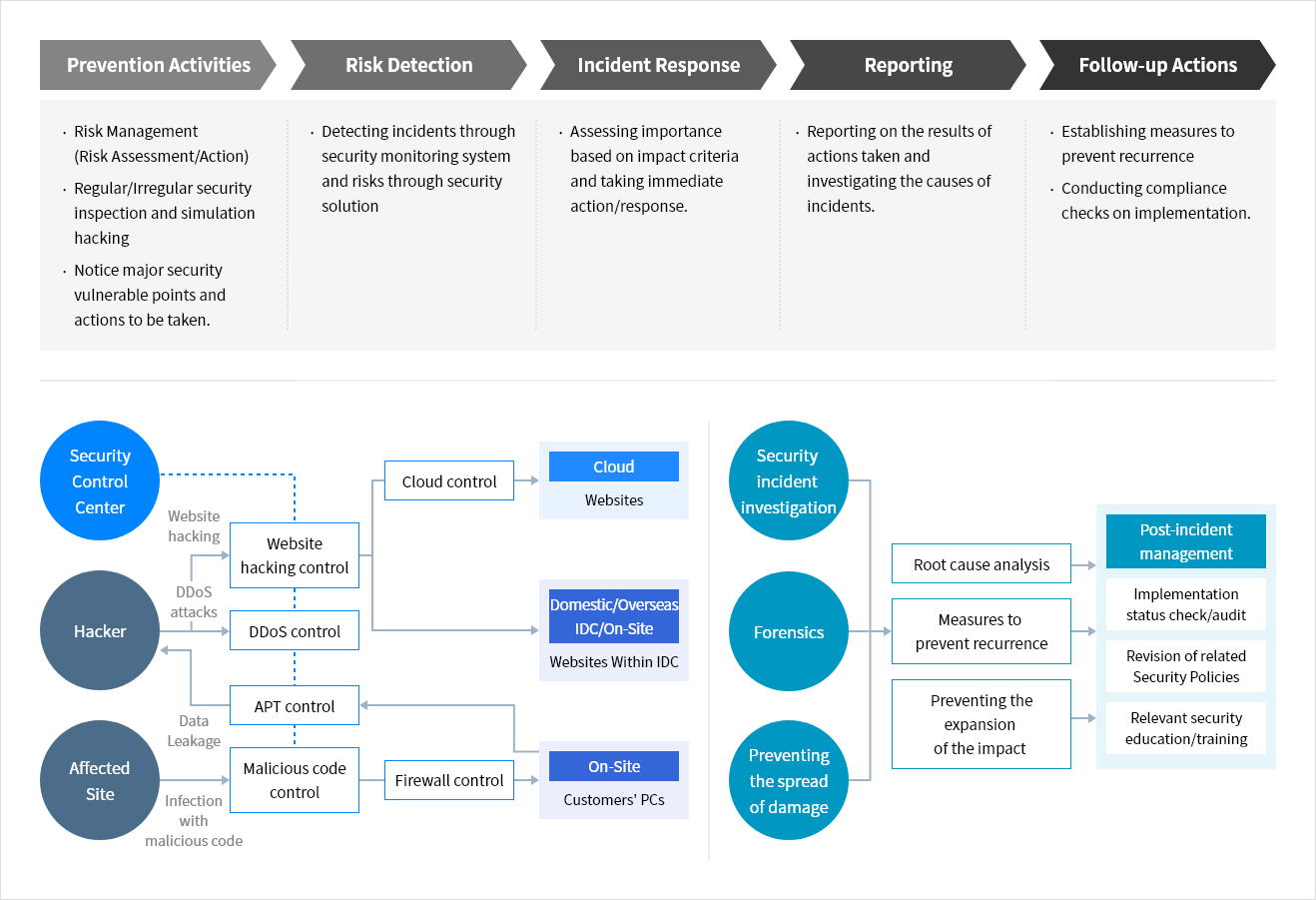
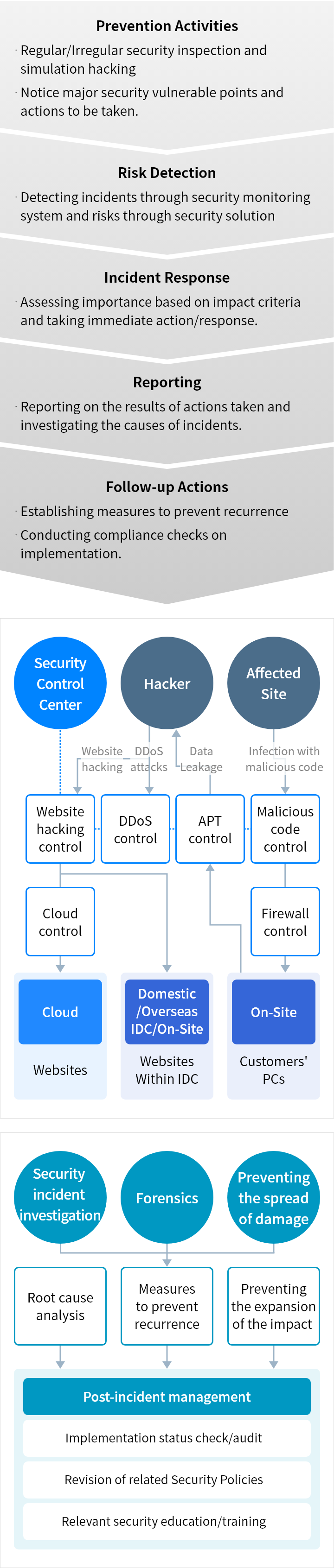
Samsung SDS's security management system, including servers, networks, databases, application systems, cloud services and others, protects the company's information assets and secures the services. Regular audits are conducted to ensure compliance and effectiveness.
Samsung SDS has established standards for access rights, user accounts, encryption of sensitive information, remote access, and other security aspects for all information systems. Systems are managed in a manner that considers the security vulnerabilities and operational characteristics of each system, ensuring they are used securely within approved boundaries. In addition, Samsung SDS conducts regular security assessments, including penetration testing and security reviews, to protect services and internal data, and to prepare for new vulnerabilities.