
From March 14th to 16th, SECON (International Security Exhibition & Conference) was held for 3 days at Kintex, Korea. The SECON exhibition takes place every March and attracts a great deal of attention from IT and security companies around the world. Let’s take a look at the onsite excitement of SECON 2018.
A total of 20 countries participated in the SECON 2018, the only overall integrated security exhibition in Asia. More than 430 security companies and 1,000 booths were set up in the exhibition with over 40,000 visitors attending them.
I was able to get a glimpse of the latest security technologies and trends at the event. Additionally, I was able to check out the latest new products and technologies.
Particularly, I was able to experience and see the most widely used security technology of 2018, the biometric authentication and image analysis.
Biometric Technology
Let’s first take a look at biometric technologies.
According to AMI, a market researching company, the global biometric market will surge from 2.6 billion US dollars in 2015 to 34.6 billion US dollars in 2020. As Samsung SDS is also at the forefront of biometric identification technology with Nexsign solution, I attended the exhibition with much attention.
The biometric authentication technologies exhibited at SECON 2018 were divided into three categories; fingerprint recognition, facial recognition, and iris recognition.
Fingerprint Recognition
It is the most widely used biometric authentication technology. However, since it is most widely used, security is somewhat in danger of exposure. With such risks at hand, in the event, it showed a technique to prevent counterfeit fingerprints by using silicon. The main techniques used to prevent counterfeit fingerprints are Dynamic Change Pattern Analysis and Liveness Feature Analysis. It demonstrated a demo where the recognition technique detected every little minute details of a fingerprint.
Also, I was able to see a variety of biometric authentication technologies such as face and finger print recognition, or finger print, finger vein, and palm recognition used together in order to increase security. I was able to see the advancement in the biometric technology as they came together.
Face Recognition
Previously, face recognition technology was used to analyze images only using one camera to analyze a specific person. However, now with the ability to analyze IR (Infrared Radiation) images, we are able to improve the security and reliability of our customer’s security. Additionally, technologies that combine card tagging modules were also noticeable. S1’s CLES register, Suprema’s face recognition terminal, and HiKVision’s fingerprint recognition terminal that has integrated stereo camera, were among the ones that really stood out.

Iris Recognition
Iris recognition is more accurate than the previous two authentication technologies. Unlike fingerprints, iris does not change over time. On the other hand, it is difficult for the technology to recognize the iris when one is wearing glasses or contact lenses or when the sun is too bright, so some techniques were also introduced which improved on this area.
Image analysis technology.
Looking at the image analysis technology, they presented a bigger picture in terms of facial analysis, object analysis, and other miscellaneous analyses.
Facial Analysis
At the event not only did facial analyzer decipher the gender and age of a face but it also introduced techniques that matched faces of the same person detected at different locations or techniques for searching faces that has similar characteristics.
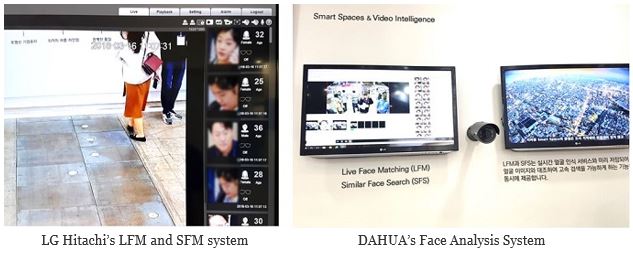
Object Analysis
Object analysis Technologies for analyzing object patterns and analyzing abnormal situations by recognizing human postures, were introduced.

Miscellaneous Analysis
Miscellaneous analytical techniques have introduced variety of technologies that were higher in practicality and usability. One of them was a technology used to analyze the traffic volume of the streets as well as search for a particular individual vehicles or to detect abnormal behaviors of the vehicles.
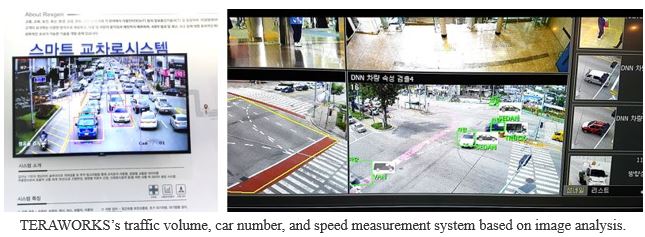

In addition to the biometric authentication and image analysis technologies, the two main part of the SECON 2018 exhibition, I was able to access various technologies such as solution introducing technology using augmented reality, face recognition door bells, and unmanned stores.

SECON 2018, the showcase for top of the line security technologies, showed me that there is a growing interest in security. As hacking technology evolve, it was evident that there was a necessity for enhancing our security.
Inseok Luke Seo Professional_AI Research Center_Samsung SDS

