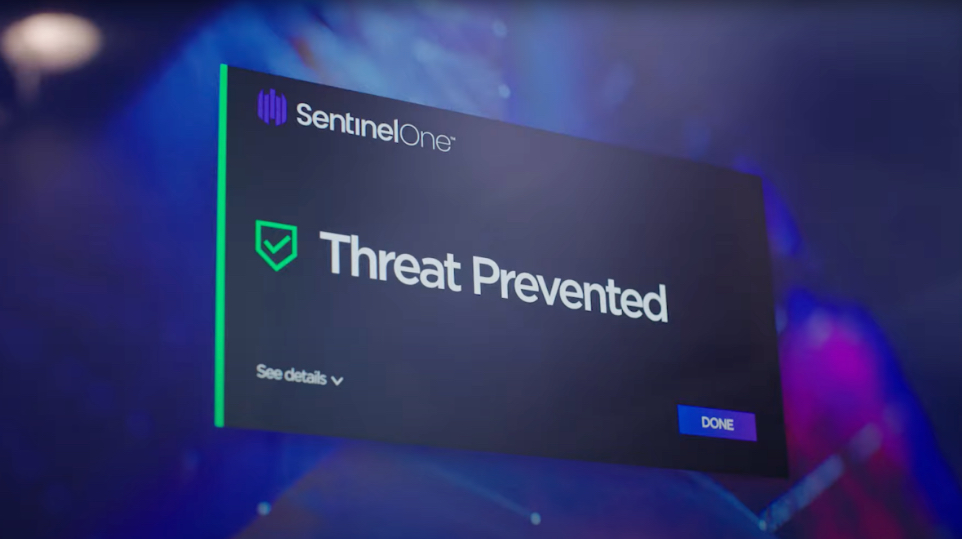
SentinelOne
AI based Endpoint Detect & Response Solution
Reduce your endpoint risk and enhance efficiency with AI in security
Expected effect
- It effectively responds to Zero-Day attacks, such as Ransomware, which is not detected by signature-based vaccines, and unknown malicious codes, and securely protects corporate information assets with specialized Ransomware damage recovery features for SentinelOne endpoint solutions.


-
Agent-based integrated management of endpoints
Provides a strong response to efficient management and advanced security threats in complex endpoint environments based on a single Agent & Single Management Console.
-
Block and detect security threats in real time
Block an intrusion of malicious files by analyzing suspicious devices in endpoints, and respond threats (file-less/in-memory, exploit, malicious scripts and credential) to bypass the existing systems in real time.
-
AI based real-time threat response
Risk monitoring and AI analytics (process/network/registry event) allow to recognize and respond threats quickly, reducing the time to Reduce intrusion response time.
-
Flexible scalability
With the minimum use of resources and no pressure on endpoint’s performance such as PC, server, etc, SentinelOne supports Windows, Mac, Linux and other OS and VDI settings to expand security coverage.
Videos
SentinelOne provides real-time response from all security threats at every stage of the threat life cycle and complete transparency against any threats that occur over the network.
Use Cases
SentinelOne, more adaptability in security
-
 AI based Analysis of security attacksAutomatically analyze IOC(Indicator of compromise) at endpoints and sense responding workflows to gain important insights, thus reducing a threat response time.
AI based Analysis of security attacksAutomatically analyze IOC(Indicator of compromise) at endpoints and sense responding workflows to gain important insights, thus reducing a threat response time. -
 Block and Recover for RansomewareDefend unknown new/variant Ransomware by preventing the execution of suspected processes with Ransomware in an on / offline environment.
Block and Recover for RansomewareDefend unknown new/variant Ransomware by preventing the execution of suspected processes with Ransomware in an on / offline environment. -
 Simple security operation
Simple security operation
Single agent and management console covers vaccine and patch management, prevention of personal information leaks, vulnerable system check and action taking as well as detection of endpoint threat, realizing a simple and integrated operation.
Security Control Response System
SentinelOne Cyber Threat Response system
basically includes anti-virus features that detect based on signature or reputation, Static / dynamic AI engines respond to threats from malicious code with pattern and behavior-based detection, blocking, and response automation, and prepare for potential threats through attack analysis and threat hunting.
- Signature-based vaccine
- File Reputation based Vaccine
- Heuristic based vaccine
- AI based vaccine
- Zero-day attack blocking
- Fileless attack blocking (memory, script attack, etc.)
- Anomaly-based detection
- Log Analysis / Accident Analysis
- device control
- Workflow Automation for Accident Response
- Recovery of data damage by Ransomware, etc.
Replacement of existing vaccine function
더하기
Static AI based detection function
Dynamic AI Detection: Behavior Monitoring
더하기
Accident response function
Major features
-
Real-time workflow and threat blockage
A Kernel-based monitoring with patent acquired searches endpoint IOC easily and simply to respond to security threats strongly.
-
Active suspicious file control and firewall management
Business settings and security requirements support an active suspicious file control and firewall management, blocking the inflow of malicious code from multiple PC sources completely.
-
Block advanced memory attacks
Block an exploitation of attacks in memory, not in files, normal tools (MS Shell), and malicious active scripts and macros. Even block advanced attacks under scripts such as VBA.
-
Perfect Recovery from Ransomware Infection
Detect and neutralize attacks by malicious codes (ransom wares etc), and treat them by recovering back to a status before attack. Its own technology protects with backup folders, so important files are safe and secured even if they are infected by ransomware.
Related Offerings
Find out more about our offerings
Enabling authorized users to access information assets more easily with one single authentication. Reinforcing account security through access management and abnormal authentication monitoring.
Enhance your endpoint security posture by effectively managing and controlling endpoint security threats
With the work automation solution to operate firewalls, human errors will be prevented when operating firewalls of multiple vendors. Through rule optimization, policy-related errors can be prevented.
Database encryption service for enterprises to protect data with its verified security. Protect your personal information and important data from the data leaks and hacking that occur in many cloud servers and on-premise environment.
To protect in-house assets from cyber attacks, you need to prevent any threats and the spread of malicious codes through multilateral analysis. Protect business assets through systematic techniques and a quick response process against APT attacks.
Security service that detects website attacks by using AI. Protect your websites safely with up-to-date attack tactics.
Detect the abuse of inside business information with big data-based scenarios and behavioral pattern analysis. It always monitors the use of proprietary information and sends warnings for any unusual activity. Prevent information leakage in advance.
Whether you’re looking for a specific business solution or just need some questions answered, we’re here to help